Access Server Security Policy
A set of standard Active Directory domain group policies recommended for use on a server performing the Axidian Privilege Gateway role to ensure security.
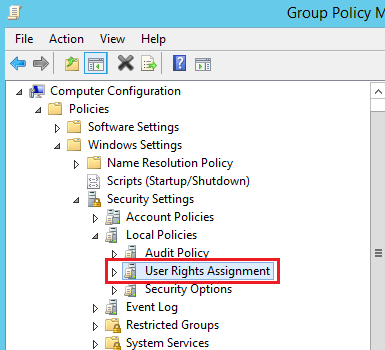
User Rights Assignment Section
Computer Configuration → Policies → Windows Settings → Security Settings → Local Policies → User Rights Assignment
Description of policies
| Policy | Description | Values |
|---|---|---|
| Access Credential Manager as a trusted caller | This setting is used by Credential Manager during backup and recovery. This privilege should not be granted to accounts as it is only granted by Winlogon. Users' stored credentials can be compromised if this privilege is granted to others. | Undefined |
| Act as part of the operating system | This user right allows a process to impersonate any user without authentication. The process can thus access the same local resources as the user. Processes that require this privilege must use a LocalSystem account that already contains this privilege, rather than a separate user account with this privilege. If your organization only uses servers running the Windows Server 2003 family of operating systems, there is no need to assign this privilege to users. However, if your organization has servers running Windows 2000 or Windows NT 4.0, you may need to assign this privilege to users to make them possible to use applications that exchange passwords in plain text format. Attention! Assigning this right to a user may pose a security risk. Assign such rights only to trusted users. | Undefined |
| Adjust memory quotas for a process | This privilege determines who can change the maximum amount of memory used by a process. This user right is defined in the default domain controller's Group Policy Object (GPO) and in the local workstation and server security policy. Note. This privilege is useful when configuring a system, but its use can be harmful in such cases like attacks of type service denial. | NT AUTHORITY\NETWORK SERVICE, NT AUTHORITY\LOCAL SERVICE, BUILTIN\Administrators |
| Allow log on locally | This setting determines who can log on to the computer. | BUILTIN\Administrators |
| Allow log on through Remote Desktop Services | This security setting determines which users or groups have permission to log on as a Remote Desktop Services client. | BUILTIN\Administrators |
| Back up files and directories | This user right determines which users can override permissions on files, directories, the registry, and other persistent objects for the purpose of system backup. Specifically, this user right is similar to granting the following permissions to a user or group on all folders and files on the system: - Browse Folders/Execute Files - Folder Contents/Read Data - Reading attributes - Reading extended attributes - Reading Permissions Attention! Assigning this right to a user may pose a security risk. Since it is impossible to know exactly what the user is doing with the data - creating an archive, stealing or copying for distribution - assign this right only to trusted users. | BUILTIN\Administrators |
| Bypass traverse checking | This user right controls which users can browse directory trees, even if those users do not have directory permissions. This privilege does not allow users to view the contents of the directory, only browsing. | BUILTIN\Administrators, NT AUTHORITY\Authenticated Users, NT AUTHORITY\LOCAL SERVICE, NT AUTHORITY\NETWORK SERVICE |
| Change the system time | This user right determines which users and groups can change the time and date of the computer's internal clock. Users with this right can influence the view of event logs. If the system time has been changed, the tracked event entries will reflect the new time rather than the actual time the events occurred. | BUILTIN\Administrators, NT AUTHORITY\LOCAL SERVICE |
| Change the time zone | This user right determines which users and groups can change the time zone that the computer uses to display local time, which is the sum of the computer's system time and the time zone offset. The system time itself is absolute and does not change when you change the time zone. | BUILTIN\Administrators, NT AUTHORITY\LOCAL SERVICE |
| Create a token object | This security setting determines which accounts can be used by processes to create tokens, which can then be used to gain access to any local resources if the process uses an internal interface (API) to create the access token. This right is used by the operating system for internal purposes. Unless necessary, do not grant this right to any user, group, or process other than the Local System user. Attention! Assigning this right to a user may pose a security risk. Do not assign this right to a user, group, or process that you do not want to be allowed to control the system. | Undefined |
| Create global objects | This security setting determines whether users can create global objects that are available to all sessions. Users can still create objects for their sessions without this right. The creation of global objects can affect processes running in other users' sessions, leading to application errors and data corruption. Attention! Assigning this right to a user may pose a security risk. Assign it only to trusted users. | BUILTIN\Administrators, NT AUTHORITY\SERVICE |
| Create permanent shared objects | This user right controls which accounts can be used by processes to create a directory object using the Object Manager. This user right is used internally by the operating system and is useful for kernel-mode components that extend an object's namespace. Because this right is already assigned to components running in kernel mode, it does not need to be specifically assigned. | Undefined |
| Create symbolic links | This privilege defines the ability for a user to create symbolic links from the computer they are logged on to. Attention! Assign it only to trusted users. Symbolic links can expose vulnerabilities in applications that are not designed to handle them. | BUILTIN\Administrators |
| Debug programs | This user right controls which users can attach a debugger to any process or kernel.This right does not need to be assigned to developers who are debugging their own applications. Developers will need it to debug new system components. This user right provides full access to important operating system components. Attention! Assigning this right to a user may pose a security risk. Assign it only to trusted users. | BUILTIN\Administrators |
| Deny access to this computer from the network | This security setting determines which users are denied access to the computer from the network. This setting replaces the Allow access to this computer from the network policy setting if both policies apply to the user account. | BUILTIN\Guests |
| Deny log on as a batch job | This security setting determines which accounts are denied login as a batch job. This setting replaces the Allow logon as a batch job option if both options apply to the user account. | BUILTIN\Guests |
| Deny log on as a service | This security setting determines which service accounts are denied to execute registration of a process as a service. This policy setting replaces the "Allow logon as a service" setting if both options apply to the user account. Note. This security setting does not apply to the System, Local Service, or Network Service accounts. | BUILTIN\Guests |
| Deny log on locally | This security setting determines which users are denied to log on. This policy setting replaces the Allow local logon setting if both policies apply to the account. Attention! If this security setting is applied to the Everyone group, no one will be able to log on locally. | BUILTIN\Guests |
| Deny log on through Terminal Services | This security setting determines which users and groups are prohibited from logging on as a Remote Desktop Services client. | BUILTIN\Guests |
| Enable computer and user accounts to be trusted for delegation | This security setting determines which users can set the Delegation Allowed setting for a user or computer object. A user or object after getting this privelege will have write access to control flags of the user account or computer object. A server process running on a computer (or in a user context) that has delegation enabled can access the resources of another computer using the client's delegated credentials until the "Account cannot be delegated" control flag is set on the client account. This user right is defined in the default domain controller's Group Policy Object (GPO) and in the local workstation and server security policy. Attention! Improper use of this user right or the Delegation Allowed setting can leave the network vulnerable to sophisticated Trojan horse malware attacks that impersonate incoming clients and use their credentials to gain access to network resources. | BUILTIN\Administrators |
| Force shutdown from a remote system | This security setting determines which users are allowed to shut down the computer remotely. Improper use of this user right may result in a denial of service. This user right is defined in the default domain controller's Group Policy Object (GPO) and in the local workstation and server security policy. | BUILTIN\Administrators |
| Generate security audits | This security setting determines which accounts can be used by the process to write entries to the security log. The security log is used to track unauthorized access to the system. Improper use of this user right can cause multiple audit events to be generated that can hide evidence of an attack or cause a denial of service if the "Audit: Shut down system immediately if security audit logging cannot be logged" security setting is enabled. For more information, see "Audit: Shut down system immediately if security audit logging cannot be logged". | NT AUTHORITY\LOCAL SERVICE, NT AUTHORITY\NETWORK SERVICE |
| Impersonate a client after authentication | Granting a user this privilege allows programs running as that user to impersonate the client. Requiring this privilege for such impersonation prevents an unauthorized user from persuading a client to connect (for example, through a remote procedure call (RPC) or named pipes) to a service it has created and then impersonating the client, thereby elevating the client to administrative or system level privileges. Attention! Assigning this right to a user may pose a security risk. Assign such rights only to trusted users. Note. By default, the built-in Service group is added to the access tokens of services started by Service Control Manager. The built-in Service group is also added to the access tokens of COM servers that are launched by the COM framework and configured to run under a specific account. Therefore, these services receive this user right when they start. Additionally, a user can impersonate an access token if any of the following conditions are met: An impersonated access token is assigned to this user.In this login session, the user created an access token by explicitly providing login credentials.The requested level is lower than "Impersonate", for example: "Anonymous" or "Identify". Therefore, users generally do not need this user right. More information can be found by searching for SeImpersonatePrivilege in the Microsoft Platform SDK. Attention! Enabling this setting may cause programs that have this privilege to lose their Impersonate privilege and block their execution. | BUILTIN\Administrators, NT AUTHORITY\SERVICE |
| Increase scheduling priority | This security setting determines which accounts can use a process that has the Write Property right on another process to elevate the execution priority assigned to the other process. A user with this privilege can change the execution priority of a process through the Task Manager user interface. | BUILTIN\Administrators |
| Load and unload device drivers | This user right determines which users can dynamically load and unload device drivers or other kernel-mode code. This user right does not apply to Plug and Play device drivers. It is not recommended to assign this privilege to other users. Attention! Assigning this right to a user may pose a security risk. Do not assign this right to a user, group, or process that you do not want to be allowed to control the system. | BUILTIN\Administrators |
| Lock pages in memory | This security setting determines which accounts can use processes to save data to physical memory to prevent that data from being flushed to virtual memory on disk. Using this privilege can significantly impact system performance by reducing the amount of available random access memory (RAM). | Undefined |
| Log on as a batch job | This security setting allows the user to log on using a tool that uses a batch job queue, and is provided only for compatibility with previous versions of Windows. For example, if a user submits a job using the Job Scheduler, the Job Scheduler logs the user into the system as a batch logon user rather than as an interactive user. | BUILTIN\Administrators |
| Manage auditing and security log | This security setting determines which users can specify object access audit settings for individual resources, such as files, Active Directory objects, and registry keys. This security setting does not allow the user to enable auditing of access to files and objects in general. To enable such auditing, you need to configure the access parameter to the "Audit" object in the path "Computer Configuration\Windows Settings\Security Settings\Local Policies\Audit Policies". Audit events can be viewed in the Event Viewer security log. A user with this privilege can also view and clear the security log. | BUILTIN\Administrators |
| Modify an object label | This privilege determines which user accounts are allowed to change the integrity labels of objects, such as files, registry keys, or processes that are owned by other users. Processes running under a user account without this privilege can demote the label level of an object that the user owns. | Undefined |
| Modify firmware environment values | This security setting determines who can change the hardware environment settings. Hardware environment variables are settings stored in the non-volatile memory of non-x86 computers. The parameter depends on the processor. On x86 computers, the only hardware environment value that can be changed by assigning this user right is the Last Known Good Configuration setting, which should only be changed by the system. On Itanium-based computers, boot data is stored in nonvolatile memory. This user right must be assigned to users to run the bootcfg.exe program and change the Default Operating System option in the Boot and Recovery component of the System Properties dialog box. On all computers, this user right is required to install and update Windows. Note. This security setting does not affect users who can change the system and user environment variables that appear on the Advanced tab of the System Properties dialog box. For information about how to change these variables, see Add or change the value of environment variables. | BUILTIN\Administrators |
| Perform volume maintenance tasks | This security setting determines the users and groups that can perform volume maintenance tasks, such as remote defragmentation. Be careful when assigning this user right. Users with this right can browse disks and add files to memory occupied by other data. After opening additional files, the user can read and change the requested data. | BUILTIN\Administrators |
| Profile single process | This security setting determines the users who can use performance monitoring tools to monitor the performance of non-system processes. | BUILTIN\Administrators |
| Profile system performance | This security setting determines the users who can use performance monitoring tools to monitor the performance of system processes. | BUILTIN\Administrators |
| Replace a process level token | This security setting determines the user accounts that can call the API procedure CreateProcessAsUser() to allow one service to start another. The Task Scheduler is an example of a process that uses this user right. For information about the Task Scheduler, see the Task Scheduler overview. | NT AUTHORITY\LOCAL SERVICE, NT AUTHORITY\NETWORK SERVICE |
| Restore files and directories | This security setting defines users who can bypass permissions on files, directories, the registry, and other persistent objects when restoring backup copies of files and directories, and users who can make any valid security principal the owner of an object. Specifically, this user right is similar to granting the following permissions to a user or group on all folders and files on the system: - Browse Folders/Execute Files -Write Attention! Assigning this right to a user may pose a security risk. Assign it only to trusted users, because this setting allows the user to overwrite registry settings, hide data, and take ownership of system objects. | BUILTIN\Administrators |
| Shut down the system | This security setting determines which users can shut down the operating system by using the Shut Down command after logging on locally. Improper use of this user right may result in a denial of service. | BUILTIN\Administrators |
| Take ownership of files or other objects | This security setting determines the users who can take ownership of any securable system object, including: Active Directory objects, files and folders, printers, registry keys, processes, and threads. Attention! Assigning this right to a user may pose a security risk. Assign it only to trusted users, because objects are fully controlled by their owners. | BUILTIN\Administrators |
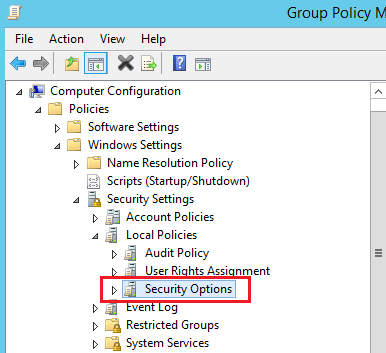
Security Options Section
Computer Configuration → Policies → Windows Settings → Security Settings → Local Policies → Security Options
Accounts
Description of policies
| Policy | Description | Values |
|---|---|---|
| Accounts: Administrator account status | This security setting determines whether the local administrator account is enabled or disabled. Notes. If the current administrator's password does not meet the password requirements, you will not be able to re-enable the administrator account if it was previously disabled. In this case, the administrator account password must be reset by another member of the administrators group. For information, see Reset Your Password overview. Disabling the administrator account may hinder maintenance in some circumstances. When restarting in Safe Mode, a disabled administrator account can only be enabled if the computer is not joined to a domain and there are no other active local administrator accounts. If the computer is joined to a domain, the disabled administrator account cannot be enabled. | Enabled |
| Accounts: Guest account status | This security setting determines whether the guest account is enabled or disabled. Note. If the guest account is disabled and the Network Access: Sharing and security model for local accounts security setting is set to Guests only, network logon attempts made by, for example, Microsoft Network Server (SMB service) will fail. | Disabled |
| Accounts: Limit local account use of blank passwords to console logon only | This security setting determines whether local accounts that are not password-protected can be used to sign in from locations other than the computer's physical console. If enabled, local accounts that are not password protected can only log in using the computer keyboard. Attention! Computers located in physically unsecured locations should always enforce strong password settings for all local user accounts. Otherwise, any user with physical access to the computer can log in using a user account that does not have a password. This is especially important for laptop computers. If this security setting is applied to the Everyone group, no one will be able to log on through Remote Desktop Services. Notes. This setting has no effect if domain accounts are used to log in. Applications that use remote interactive logon can bypass this setting. | Enabled |
Audit
Description of policies
| Policy | Description | Values |
|---|---|---|
| Audit: Audit the use of Backup and Restore privilege | This security setting determines whether the use of all user privileges, including backup and restore, will be audited when the "Audit privilege use" policy is enabled. When the "Audit privilege use" policy is enabled, enabling this setting generates an audit event for each file that is backed up or restored. If this security setting is disabled, backup and restore privilege usage is not audited even if the "Audit privilege usage" option is enabled. Note. In versions of Windows earlier than Vista, changes made by configuring this security setting will not take effect until you restart Windows. Enabling this setting can cause a very large number of events (sometimes several hundred per second) during archiving. | Enabled |
Devices
Description of policies
| Policy | Description | Values |
|---|---|---|
| Devices: Allowed to format and eject removable media | This security setting determines who is allowed to format and eject NTFS removable media. | Administrators |
| Devices: Prevent users from installing printer drivers | For a local computer to use a shared printer, the shared printer driver must be installed on this local computer. This security setting determines who is allowed to install the printer driver when adding a shared printer. If this setting is enabled, only administrators can install the printer driver when adding a shared printer. If this option is disabled, anyone can install the printer driver when adding a shared printer. Notes. This setting does not affect the ability to add a local printer. This setting does not affect administrators. | Enabled |
| Devices: Restrict CD-ROM access to locally logged-on user only | This security setting determines whether the CD drive is accessible to both local and remote users. When enabled, access to CDs is limited to users who are logged on interactively. If this option is enabled and no one is logged on interactively, the CD drive will be accessible over the network. | Enabled |
| Devices: Restrict floppy access to locally logged-on user only | This security setting determines whether a removable floppy drive can be accessed by both local and remote users. When this setting is enabled, access to removable floppy drives is limited to users who are logged on interactively. If this option is enabled and no one is logged on interactively, the floppy drive will be accessible over the network. | Enabled |
Interactive Logon
Description of policies
| Policy | Description | Values |
|---|---|---|
| Interactive logon: Do not display last user name | This security setting determines whether the Windows logon screen displays the name of the last user logged on to this computer.If this policy is enabled, the username will not be displayed. | Enabled |
| Interactive logon: Do not require CTRL+ALT+DEL | This security setting determines whether CTRL+ALT+DEL is required before logging on. If this policy is enabled, you do not need to press CTRL+ALT+DEL before logging on. Not requiring users to press CTRL+ALT+DEL before logging in leaves users vulnerable to password sniffing attacks. Mandatory CTRL+ALT+DEL key presses before logging in ensure that data is transmitted over a trusted channel when users enter passwords. If this policy is disabled, pressing CTRL+ALT+DEL is required for any user before logging on to Windows. | Disabled |
| Interactive logon: Number of previous logons to cache (in case domain controller is not available) | The login information for each unique user is cached locally to ensure that logon is possible if the domain controller is not accessible during subsequent logon attempts. Cached login information is stored from the previous session. If the domain controller cannot be accessed and the user's logon information is not cached, the following message appears: "There are currently no login servers available to service your login request". For this policy setting, a 0 value disables login caching. Any value above 50 only caches 50 login attempts. Windows supports a maximum of 50 cache entries, with the number of entries consumed per user depending on the credentials. For example, Windows can cache up to 50 unique user accounts with passwords, but no more than 25 user accounts with a smart card, because both password and smart card information are stored. When a user with cached login information logs on again, that user's cached information is replaced with new data. | 0 logons |
| Interactive logon: Require Domain Controller authentication to unlock workstation | To unlock a locked computer, you must provide login information. For domain accounts, this security setting determines whether a domain controller must be contacted to unlock the computer. If this setting is disabled, the user can unlock the computer using cached credentials. If this setting is enabled, the domain account used to unlock the computer must be verified as authentic by the domain controller. | Enabled |
Microsoft Network Client
Description of policies
| Policy | Description | Values |
|---|---|---|
| Microsoft network client: Send unencrypted password to third-party SMB servers | When this security setting is enabled, the Server Message Block (SMB) redirector is allowed to send cleartext passwords to non-Microsoft SMB servers that do not support password encryption during authentication. Sending unencrypted passwords poses a security risk. | Disabled |
Network Access
Description of policies
| Policy | Description | Values |
|---|---|---|
| Network access: Allow anonymous SID/Name translation | This policy setting determines whether an anonymous user can query another user's security identifier (SID) attributes. If this policy is enabled, then an anonymous user can request the SID of any other user.For example, an anonymous user who knows the administrator's SID can connect to a computer that has this policy enabled and obtain the administrator's name. This setting affects both the SID to name conversion and the reverse conversion (name to SID). If this policy setting is disabled, an anonymous user cannot request another user's SID. | Disabled |
| Network access: Do not allow anonymous enumeration of SAM accounts | This security setting determines what additional permissions are given to anonymous connections to this computer. Windows allows anonymous users to perform certain actions, such as listing domain account names and network shares. This is useful, for example, when an administrator needs to grant access to users in a trusted domain that does not support mutual trust. This security setting allows you to place additional restrictions on anonymous connections. Enabled: Do not allow enumeration of SAM accounts. This setting replaces the Everyone setting with the Authenticated in security permissions for resources. Disabled: No additional restrictions. Default permissions are used. | Enabled |
| Network access: Do not allow anonymous enumeration of SAM accounts and shares | This security setting determines whether anonymous users are allowed to enumerate SAM accounts and shares. Windows allows anonymous users to perform some actions (for example, enumeration domain account names and shared folders). This is useful if an administrator wants to grant access to users in a trusted domain that does not support mutual trust. Enable this setting to prevent anonymous users from enumerating SAM accounts and shares. | Enabled |
| Network access: Do not allow storage of passwords and credentials for network authentication | This security setting determines whether Credential Manager stores passwords and credentials during domain authentication (for later use). If this setting is enabled, Credential Manager does not save passwords and credentials on this computer. If this policy setting is disabled or not set, Credential Manager will store passwords and credentials on this computer (for future use during domain authentication). Note. Changes to the configuration of this security setting will take effect only after you restart Windows. | Enabled |
| Network access: Let Everyone permissions apply to anonymous users | This security setting determines what additional permissions are given to anonymous connections to your computer. Windows allows anonymous users to perform some actions (for example, enumeration domain account names and shared folders). This is useful if an administrator wants to grant access to users in a trusted domain that does not support mutual trust. By default, the Public SID is removed from the token generated for anonymous connections. Therefore, permissions in the Public group do not affect anonymous users. When this setting is set anonymous users have access only to resources that they are explicitly allowed to access. When enabled, the Public SID is added to the token generated for anonymous connections. In this case, anonymous users have access to any resource allowed in the Public group. | Disabled |
| Network access: Named Pipes that can be accessed anonymously | This security setting determines which communication sessions (channels) will have attributes and permissions that allow anonymous access. | Undefined |
| Network access: Remotely accessible registry paths | This security setting determines which registry paths can be accessed over the network, regardless of the users or user groups specified in the access control list (ACL) of the winreg registry key. | Undefined |
| Network access: Remotely accessible registry paths and sub-paths | This security setting determines which registry paths and subpaths can be accessed over the network, regardless of the users or user groups specified in the access control list (ACL) of the winreg. | Undefined |
| Network access: Restrict anonymous access to Named Pipes and Shares | When enabled, this security setting restricts anonymous access to shares and named pipes based on the following settings: - Network access: Allow anonymous access to named pipes - Network access: Allow anonymous access to shared resources | Enabled |
| Network access: Shares that can be accessed anonymously | This security setting determines which shares anonymous users can access. | Undefined |
| Network access: Sharing and security model for local accounts | This security setting determines how local accounts are authenticated when logging on to the network. If this setting is set to Normal, when you log on to the network with local account credentials, authentication is performed using those credentials. Setting the Normal value allows more flexible control of access to resources. It can be used to provide different types of access to different users to the same resource.When this setting is set to Guest, network logins using local account credentials are automatically mapped to the guest account. When setting the Guest value there is no difference between users. All users are authenticated with a guest account and given the same level of access to that resource — Read Only or Modify. By default on domain computers: Normal. By default on standalone computers: Guest. Attention! If the guest model is used, any user who has access to the computer over the network (including anonymous Internet users) can access shared resources. To protect your computer from unauthorized access, you must use Windows Firewall or another similar program. Additionally, when setting the Normal, local accounts must be password protected so that they cannot be used to access system shares. Note. This setting does not affect interactive logon operations that are performed remotely by using services such as Telnet or Remote Desktop Services. | Classic - local users authenticate as themselves |
Network Security
Description of policies
| Policy | Description | Values |
|---|---|---|
| Network security: Do not store LAN Manager hash value on next password change | This security setting determines whether the LAN Manager (LM) hash value for the new password should be stored the next time the password is changed. The LM hash is relatively weak and vulnerable to attack compared to the more secure Windows NT hash. Since the LM hash is stored in the security database on the local machine, if the security database is attacked, the passwords can be decrypted. | Enabled |
| Network security: Force logoff when logon hours expire | This security setting determines whether users are logged out when they connect to the local computer outside of the logon time that is configured for their account. This setting affects the Server Message Block (SMB) component. When this policy is enabled, client sessions with the SMB server are forced to terminate after the client logon timeout expires. If this policy is disabled, the client's session is retained after the client's login timeout expires. Note. This security setting is applied in the same way as an account policy. Domain accounts can only have one account policy. The account policy must be defined in the default domain policy; it is enforced by controllers in that domain. A domain controller always gets its account policy from the Default Domain Policy Group Policy Object (GPO), even if there is another account policy that applies to the organizational unit that contains that domain controller. By default, workstations and servers that are members of a domain receive the same account policy for their local accounts. However, the local account policies of these computers may differ from the domain account policies if an account policy is defined for the organizational unit that contains these computers. Kerberos settings do not apply to such computers. | Enabled |
| Network security: LAN Manager authentication level | This security setting determines which challenge-response authentication protocols are used for network logon. The value of this setting affects the level of authentication protocol that clients use, the level of negotiated session security, and the level of authentication accepted by servers as follows. Send LM and NTLM responses: Clients use LM and NTLM authentication and never use NTLMv2 session security; Domain controllers accept LM, NTLM, and NTLMv2 authentication. Send LM and NTLM - Use NTLMv2 session security when negotiating: Clients use LM and NTLM authentication, and NTLMv2 session security if the server supports it; Domain controllers accept LM, NTLM, and NTLMv2 authentication. Send NTLM response only: Clients use only NTLM authentication, and use NTLMv2 session security if the server supports it; Domain controllers accept LM, NTLM, and NTLMv2 authentication. Send NTLMv2 response only: Clients use only NTLMv2 authentication, and use NTLMv2 session security if the server supports it; Domain controllers accept LM, NTLM, and NTLMv2 authentication. Send only NTLMv2 response and refuse LM: Clients use only NTLMv2 authentication, and use NTLMv2 session security if the server supports it; Domain controllers reject LM (accepting only NTLM and NTLMv2 authentication). Send only NTLMv2 response and refuse LM and NTLM: Clients use only NTLMv2 authentication, and use NTLMv2 session security if the server supports it; Domain controllers reject LM and NTLM (accepting only NTLMv2 authentication). | Send NTLMv2 response only. Refuse LM & NTLM |
| Network security: Minimum session security for NTLM SSP based (including secure RPC) clients | This security setting allows the client to require negotiation of 128-bit encryption and/or NTLMv2 session security. These values depend on the LAN Manager Authentication Level security setting. The following options are available: Require NTLMv2 session security. If the NTLMv2 protocol is not negotiated, the connection will not be established. Require 128-bit encryption. If 128-bit encryption is not negotiated, the connection will not be established. | Require NTLMv2 session security: Enabled Require 128-bit encryption: Enabled |
| Network security: Minimum session security for NTLM SSP based (including secure RPC) servers | This security setting allows the server to require negotiation of 128-bit encryption and/or NTLMv2 session security. These values depend on the LAN Manager Authentication Level security setting. The following options are available: Require NTLMv2 session security. If message integrity is not consistent, the connection will not be established. Require 128-bit encryption. If 128-bit encryption is not negotiated, the connection will not be established. | Require NTLMv2 session security: Enabled Require 128-bit encryption: Enabled |
Shutdown
Description of policies
| Policy | Description | Values |
|---|---|---|
| Shutdown: Allow system to be shut down without having to log on | This security setting determines whether you can shut down your computer without logging on to Windows. If this policy is enabled, the Shutdown option can be selected on the Windows logon screen. If this policy is disabled, the Shut Down command does not appear on the Windows logon screen. In this case, to shut down the system, the user must be successfully logged in and must have the Shut Down privilege. | Disabled |
| Shutdown: Clear virtual memory pagefile | This security setting determines whether the virtual memory page file is cleaned up when the system shuts down. Virtual memory support uses the system page file to swap memory pages to disk when they are not in use. While the system is running, the paging file is opened by the operating system in exclusive mode and is well protected. However, if the system is configured to allow other operating systems to boot, you must ensure that the system's page file is cleared when the system is shut down. This ensures that sensitive process memory information that may have ended up in the page file is not available to users who gain direct unauthorized access to the page file. If this policy is enabled, the system page file is cleared when the system shuts down properly. When enabled, this security setting also resets the hibernation file (hiberfil.sys) when hibernation is disabled. | Enabled |
System Settings
Description of policies
| Policy | Description | Values |
|---|---|---|
| System settings: Optional subsystems | This security setting determines which additional subsystems can be launched to support applications. This parameter allows you to specify all the subsystems that are required by your environment to support applications. | Undefined |
| System settings: Use Certificate Rules on Windows Executables for Software Restriction Policies | This security setting controls whether digital certificate processing occurs when a user or process attempts to run a program with an EXE file name extension. It allows you to enable or disable certificate rules (a type of rules of politics of restricted software using). With these policies, you can create a certificate rule that allows or denies launch of a programs signed with Authenticode, depending on digital certificate. To apply certificate rules, you must enable this security setting. When certificate rules are enabled, software restriction policies check the certificate revocation list (CRL) to ensure that the program's certificate and signature are valid. This may cause performance degradation when running signed programs. You can disable this feature. In the Trusted Publisher Properties window, clear the Publisher and Timestamp check boxes. For more information, see Trusted Publisher Settings. | Enabled |
User Account Control
Description of policies
| Policy | Description | Values |
|---|---|---|
| User Account Control: Admin Approval Mode for the Built-in Administrator account | This policy setting determines the administrator approval behavior characteristics of the built-in administrator account. Possible values: Enabled. The built-in Administrator account uses Administrator approval mode. By default, any operation that requires elevation of privilege prompts the user to confirm the operation. Disabled (default). The built-in Administrator account runs all applications with full Administrator rights. | Enabled |
| User Account Control: Allow UIAccess applications to prompt for elevation without using the secure desktop | This policy setting controls whether UIAccess applications (UIA programs) can automatically disable the secure desktop for promotion requests used by a standard user. Enabled. UIA programs, including Windows Remote Assistance, automatically disable the secure desktop for elevation requests. If the "User Account Control: Switch to secure desktop when prompted for elevation" policy setting is not disabled, the prompt appears on the user's interactive desktop rather than on the secure desktop. Disabled (default). Secure Desktop can only be disabled by the Interactive Desktop user or by disabling the "User Account Control: Switch to Secure Desktop when prompted for elevation" policy setting. | Disabled |
| User Account Control: Behavior of the elevation prompt for administrators in Admin Approval Mode | This policy setting controls the behavior of the privilege elevation prompt for administrators. Possible values: Promotion without request. Allows privileged accounts to perform an operation that requires elevation of privileges without requiring consent or entering credentials. Note. This option should only be used in highly restrictive environments. Prompt for credentials on the secure desktop. For any operation that requires elevation of privilege, the secure desktop prompts you to enter your privileged user name and password. If privileged credentials are entered, the operation continues with the user's maximum available privileges. Prompt for consent on a secure desktop. For any operation that requires elevation of privileges, the secure desktop prompts you to choose either Allow or Deny. If the user selects Allow, the operation continues with the user's maximum available privileges. For any operation that requires elevation of privileges, you are prompted to enter the user name and password for the administrator account. If valid credentials are entered, the operation continues with appropriate privileges. Prompt for consent. For any operation that requires elevation of privileges, the user is prompted to select either Allow or Deny. If the user selects Allow, the operation continues with the user's maximum available privileges. Prompt for consent for third party (non-Windows) binaries (default). When an operation for a non-Microsoft application requires elevation of privileges, you are prompted to choose Allow or Deny on the secure desktop. If the user selects Allow, the operation continues with the user's maximum available privileges. | Prompt for consent for non-Windows binaries |
| User Account Control: Behavior of the elevation prompt for standard users | This policy setting determines the behavior of the privilege escalation prompt for standard users. Possible values: Prompt for credentials (default). When an operation requires elevation of privileges, you are prompted to enter the user name and password of a user account with administrator privileges. If the user enters valid credentials, the operation continues with appropriate privileges. Automatically reject requests to escalate privileges. When an operation requires elevation of privileges, an access denied error message is displayed. Organizations whose desktop computers are used by standard users can select this policy setting to reduce the number of support calls. Prompt for credentials on the secure desktop. When an operation requires elevation of privileges, the secure desktop prompts you to enter the other user's name and password. If the user enters valid credentials, the operation continues with appropriate privileges. | Prompt for credentials on the secure desktop |
| User Account Control: Only elevate UIAccess applications that are installed in secure locations | User Account Control: Elevate privileges only for UIAccess applications installed in a secure location. This policy setting determines whether applications that request execution at the UIAccess integrity level must reside in a secure folder on the file system. Only the following folders are considered safe: - …\Program Files\, including subfolders - …\Windows\system32\ - …\Program Files (x86)\, including subfolders for 64-bit versions of Windows Note. Windows enforces mandatory PKI signature verification on any interactive application that requests execution at the UIAccess integrity level, regardless of the state of this security setting. Possible values: Enabled (default). The application will only run with the UIAccess integrity level if it is located in a secure folder on the file system. Disabled. The application will run with the UIAccess integrity level even if it is not in a secure file system folder. | Enabled |
| User Account Control: Run all administrators in Admin Approval Mode | This policy setting determines the characteristics of all User Account Control policies for the computer. If you change this policy setting, you must restart the computer. Possible values: Enabled (default). Administrator approval mode is enabled. To allow the built-in Administrator account and all other users who are members of the Administrators group to operate in Administrator Approved mode, this policy must be enabled, and all associated account control policies must also be set accordingly. Disabled. Administrator approval mode and all associated User Account Control policy settings will be disabled. Note. If this policy setting is disabled, Security Center will notify you that the overall security of the operating system has been reduced. | Enabled |
| User Account Control: Switch to the secure desktop when prompting for elevation | This policy setting determines whether elevation prompts are displayed on the user's interactive desktop or on the secure desktop. Possible values: Enabled (default). All elevation requests are displayed on the secure desktop, regardless of the prompt behavior policy settings for administrators and standard users. Disabled. All requests for elevation of rights are displayed on the user's interactive desktop. The invitation behavior policy settings for administrators and standard users are used. | Enabled |
| User Account Control: Virtualize file and registry write failures to per-user locations | This policy setting controls the redirection of failures of writing the applications to specific locations in the registry and file system. This policy setting helps to reduce the risk of applications that run as an administrator and write the data to the %ProgramFiles%, %Windir%; %Windir%\system32 folder or in the HKLM\Software... folder at run time. Possible values: Enabled (default). Application write failures are redirected at runtime to user-defined locations in the file system and registry. Disabled. Applications that write data to secure locations fail with an error. | Enabled |
Other
Description of policies
| Policy | Description | Values |
|---|---|---|
| Accounts: Block Microsoft accounts | This policy setting prevents users from adding new Microsoft accounts on this computer. If you select the "Users can't add Microsoft accounts" option, users won't be able to create new Microsoft accounts on this computer, convert local accounts to Microsoft accounts, or connect domain accounts to Microsoft accounts. This option is preferred if you want to limit the number of Microsoft accounts you can use in your organization. If you select the "Users can't add or use Microsoft accounts to sign in" option, existing Microsoft account users won't be able to sign in to Windows. Selecting this option may make logging in and management of the system unavailable to an existing administrator on the computer. If this policy is disabled or not configured (recommended), users will be able to use Microsoft accounts in Windows. | Users can't add Microsoft accounts |
| Audit: Force audit policy subcategory settings (Windows Vista or later) to override audit policy category settings | Windows Vista and later versions of Windows allow you to more precisely control your audit policy by using audit policy subcategories. Setting an audit policy at the category level will override the new subcategory audit policy feature. To allow audit policy to be managed by subcategories without having to change Group Policy, Windows Vista and later versions provide a new registry value (SCENoApplyLegacyAuditPolicy) that prevents category-level audit policy from being applied from Group Policy and the Local Security Policy administration tool. If the category level audit policy set here is inconsistent with the events generated, then the cause may be because this registry key is set. | Enabled |
| Domain member: Disable machine account password changes | Determines whether the password for a domain member's computer account needs to be changed periodically. When you enable this setting, a domain member does not attempt to change the computer account password. If this setting is disabled, the domain member attempts to change the computer account password according to the Domain Member: Maximum computer account password age setting, which defaults to every 30 days. Default: Disabled. Notes. You should not enable this security setting. Account passwords are used to establish secure communication channels between domain members and domain controllers, and between domain controllers themselves within a domain. Once communication is established, the secure channel is used to transmit sensitive data needed to perform authentication and authorization. This option should not be used to support dual boot scenarios that use the same computer account. To dual boot two installations in the same domain, give the installations different computer names. | Disabled |
| Domain member: Maximum machine account password age | This security setting determines how often a domain member will attempt to change the computer account password. | 30 days |
| Domain member: Require strong (Windows 2000 or later) session key | This security setting determines whether secure channel encrypted data requires a 128-bit key. When you join a computer to a domain, a computer account is created. Then, when the system starts, the computer account password is used to create a secure channel with the domain controller. This secure channel is used to perform operations such as NTLM pass-through authentication, LSA name or SID lookup, etc. Depending on the version of Windows used on the domain controller with which the connection is made, as well as on the parameter values: Domain Member: Digital signature or encryption of secure channel data is always required. Domain Member: Encrypt secure channel data whenever possible. All or some of the data transmitted over the secure channel will be encrypted. This policy setting determines whether encrypted secure channel data requires a 128-bit key. If this setting is enabled, a secure connection will only be established if 128-bit encryption is possible. If this setting is disabled, the key strength is negotiated with the domain controller. | Enabled |
| Interactive logon: Display user information when the session is locked | This setting determines whether additional information such as email address or domain/username is displayed with the username on the login screen. For customers running Windows 10 versions 1511 and 1507 (RTM), this setting works the same as in previous versions of Windows. Because of the addition of a new privacy setting in Windows 10 version 1607, this setting applies differently to these clients. Changes in Windows 10 version 1607 Starting with version 1607, Windows 10 has new functionality that lets you hide user information such as your email address by default, and change default settings to show this information. You can configure this functionality using the new privacy setting under Settings → Accounts → Sign-in Options. By default, the privacy setting is turned off and additional user information is hidden. This Group Policy setting defines this same functionality. Possible values: Display user name, domain and user names: If logged in locally, the user's full name is displayed. If the user signs in with a Microsoft account, the user's email address is displayed. If you are logged into a domain, the domain/username is displayed. Username Only: Displays the full name of the user who locked the session. Don't display user information: No names are displayed, but all versions of Windows older than Windows 10 will display users' full names on the change user screen. Starting with version 1607 of Windows 10, this feature is no longer supported. If this value is selected, the full name of the user who has blocked the session will be displayed on the screen. This change makes this setting consistent with the new privacy setting. To prevent any user information from being displayed on the screen, enable the Interactive Logon Group Policy setting: Do not display information about the last logged on user. Empty: Default value. Means "Undefined", but the user's full name will be displayed on the screen in the same way as if "Username Only" was selected. Hotfix for Windows 10 version 1607 If you are using Windows 10 version 1607, user information will not be displayed on the login screen even if you select "Display user name, domain and user names" because the privacy setting is disabled. If you enable this option, the data will appear on the screen. You cannot change privacy settings in groups. Instead, you can apply KB4013429 to clients running Windows 10 version 1607 so that the system behaves similarly to previous versions of Windows. Interaction with the "Prevent user from displaying account information on login screen" command. In all versions of Windows 10, only the username is displayed by default. When set to "Prevent user from displaying account information on login screen", only the user's display name will be displayed on the login screen, regardless of Group Policy settings. Users will not be able to display their information. If you do not set the "Prevent user from displaying account information on login screen" setting, you can set the "Interactive logon: Display user information if session is locked" setting to "Display user name, domain and user names" so that the screen displays additional user information such as domain\username when logging in. In this case, KB4013429 must be applied to client computers running Windows 10 version 1607. Users will not be able to hide additional information. Recommendations. Whether you can enforce this policy depends on your security requirements for the login credentials displaying. If you work with computers that store sensitive information and have monitors in unsecured locations, or if your computers with sensitive information are accessed remotely, displaying the full names of logged-in users or domain account names may be against your overall security policy. Based on your security policy, it may be appropriate to set the value to "Interactive logon: Do not display last user's credentials." | User display name only |
| Interactive logon: Machine account lockout threshold | This security setting determines the number of failed logon attempts before the computer restarts. Computers that have Bitlocker enabled to protect OS volumes will be locked. To remove the lock, you must specify the recovery key in the console. Make sure the appropriate access recovery policies are enabled. The number of unsuccessful access attempts can be specified as a number from 1 to 999. If you set this value to 0, the computer will never lock. Values between 1 and 3 will be interpreted as 4. Failed password attempts on workstations or member servers that are locked using CTRL+ALT+DEL or password-protected screen savers are considered failed login attempts. | 5 invalid logon attempts |
| Microsoft network server: Amount of idle time required before suspending session | This security setting determines how long an SMB session can elapse before it is suspended due to inactivity. Administrators can use this setting to control when the computer suspends an inactive SMB session. If client activity resumes, the session is automatically re-established. For this parameter, a value of "0" means the session will be disconnected as soon as possible. The maximum value is 99999, which is 208 days; in effect, this value disables this option. Default: parameter not defined; this means that the system treats the parameter as having a value of "15" for servers and an undefined value for workstations. | 15 minutes |
| Microsoft network server: Attempt S4U2Self to obtain claim information | This security setting is intended to support clients with systems released before Windows 8 that attempt to access a file share that requires a user request. It determines whether the local file server will attempt to use the Kerberos Service-For-User-To-Self (S4U2Self) feature to obtain network client principal requests from the client account domain. This setting only needs to be enabled if the file server uses user claims to control access to files and if it will support client principals whose accounts are in a domain with client computers and domain controllers running an operating system that was released before Windows 8. This setting should be set to Automatic (the default) so that the file server can automatically determine whether a user is required to enroll. This setting should only be explicitly set to Enabled if you have local file access policies that include user access claims. When this security setting is enabled, the Windows File Server will analyze the subject access token of the authenticated network client and determine whether the claim information is present. If there are no claims, the file server will use the Kerberos S4U2Self function to contact the Windows Server 2012 domain controller in the client account's domain and obtain a claim-aware access token for the client subject.A claim-aware token may be required to access files and folders that have a claim-based access control policy applied to them. If this setting is disabled, Windows File Server will not attempt to obtain a claims-based access token for the client principal. | Disabled |
| Microsoft network server: Disconnect clients when logon hours expire | This security setting determines whether users connected to the local computer are logged off after the allowed logon time that is configured for their account has expired. This setting affects the SMB protocol component. When enabled, client sessions with the SMB service are forced to terminate after the client's allowed logon time has expired. If this setting is disabled, the client's session is saved after the client's allowed login time has expired. | Enabled |
| Microsoft network server: Server SPN target name validation level | This policy setting controls the level of verification that the folder or printer shares computer (server) performs on the service principal name provided by the client computer when it establishes a session using the SMB protocol. The SMB protocol provides the basis for file and printer sharing and other network operations, such as remote Windows administration. The SMB protocol supports verification of the SMB server's SPN in the blob provided by the SMB client to prevent a class of attacks against SMB servers called hijack attacks. This setting affects SMB1 and SMB2. This security setting determines the level of verification that the SMB server performs on the service principal name provided by the SMB client when the client establishes a session with the SMB server. Parameters: Disabled - The SMB client SPN is not required (not checked) by the SMB server. Accept if provided by client - The SMB server accepts and validates the SPN provided by the SMB client and resolves the session if it matches the SMB server's list of SPNs. If the name does NOT match, the session for the SMB client is rejected. Require from client - The SMB client MUST send a service principal name when setting up the session, and the name supplied MUST match the SMB server to which the connection request was sent. If the SPN is not specified by the client or it does not match, the session is rejected. | Off |
| Recovery console: Allow automatic administrative logon | This security setting determines whether you must provide a password for the Administrator account to gain access to the system. When this setting is enabled, the Recovery Console does not require a password, allowing you to log in automatically. | Disabled |
| Recovery console: Allow floppy copy and access to all drives and all folders | When you enable this security setting, the Recovery Console SET command is available and allows you to set the following Recovery Console environment variables. AllowWildCards: allows wildcards to be used for some commands (such as the DEL command). AllowAllPaths: allows access to any files and folders on the computer. AllowRemovableMedia: allows you to copy files to removable media, such as floppy disks. NoCopyPrompt: cancels the warning when overwriting existing files. | Disabled |
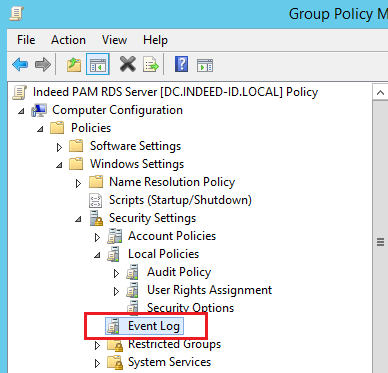
Event Log
Computer Configuration → Policies → Windows Settings → Security Settings → Event Log
Description of policies
| Policy | Description | Values |
|---|---|---|
| Maximum application log size | This security setting determines the maximum size of the application event log (max. 4 GB). In practice, a lower limit is used (approximately 300 MB). Notes. Log file sizes must be multiples of 64 KB. If you enter a value that is not a multiple of 64 KB, Event Viewer will set the log file size to a multiple of 64 KB. This setting is not included in the local computer policy object.The file size and how log events are rewritten should be specified based on the business and security requirements determined when developing the enterprise security plan. You can implement these event log settings at the site, domain, or organizational unit level to take advantage of Group Policy settings. | 100032 KB |
| Maximum security log size | This security setting determines the maximum size of the security event log (maximum 4 GB). In practice, a lower limit is used (approximately 300 MB). | 100032 KB |
| Maximum system log size | This security setting determines the maximum size of the system event log (max. 4 GB). In practice, a lower limit is used (approximately 300 MB). | 100032 KB |
| Prevent local guests group from accessing application log | This security setting determines whether guests are denied to access to the application event log. Notes. This setting is not included in the local computer policy object. | Enabled |
| Prevent local guests group from accessing security log | This security setting determines whether guests are denied to access to the security event log. Notes. This setting is not included in the local computer policy object. | Enabled |
| Prevent local guests group from accessing system log | This security setting determines whether guests are denied to access to the security event log. Notes. This setting is not included in the local computer policy object. | Enabled |
| Retention method for application log | This security setting determines how the application log is rewritten. If you are not archiving the application log, in the Properties dialog box for this policy, select the Define this policy setting check box, and then select Overwrite events when necessary. If you want to archive the log at specified intervals, select the Define this policy setting check box in the Policy's Properties dialog box, then select Overwrite old events by day and specify the number of days you want using the Keep events logged option. applications". Make sure that the maximum application log size is large enough so that it is not reached within this period of time. If you want all events to be logged, select the Define this policy setting check box in the Policy's Properties dialog box, and then select Do not overwrite events (clear log manually). If you select this option, you must manually clear the log. In this case, after the maximum log size is reached, new events are rejected. Note. This setting is not included in the local computer policy object. | As needed |
| Retention method for security log | This security setting determines how the security log is overwritten. Notes. This setting is not included in the local computer policy object. To access the security log, the user must have the Manage Audit and Security Log privelege. | As needed |
| Retention method for system log | This security setting determines how the system log is overwritten. Note. This setting is not included in the local computer policy object. | As needed |
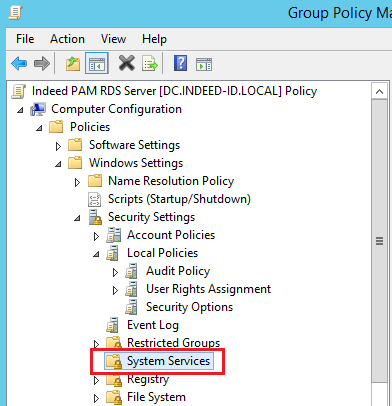
System Services
Computer Configuration → Policies → Windows Settings → Security Settings → System Services
Description of policies
| Service Name (Service Startup Mode) | Permissions | Audit |
|---|---|---|
| Routing and Remote Access (Startup Mode: Disabled) | Undefined | Undefined |
| Special Administration Console Helper (Startup Mode: Disabled) | Undefined | Undefined |
| SNMP Trap (Startup Mode: Disabled) | Undefined | Undefined |
| Telephony (Startup Mode: Disabled) | Undefined | Undefined |
| Windows Error Reporting Service (Startup Mode: Disabled) | Undefined | Undefined |
| WinHTTP Web Proxy Auto-Discovery Service (Startup Mode: Disabled) | Undefined | Undefined |
File System
Computer Configuration → Policies → Windows Settings → Security Settings → File System
%SystemRoot%\System32\config
Description of policies
Configure this file or folder then: Propagate inheritable permissions to all subfolders and files
Permissions
| Type | Value | Access | Applies To |
|---|---|---|---|
| Allow | ALL APPLICATION PACKAGES | Read and Execute | This folder, subfolders and files |
| Allow | CREATOR OWNER | Full Control | Subfolders and files only |
| Allow | NT AUTHORITY\SYSTEM | Full Control | This folder, subfolders and files |
| Allow | BUILTIN\Administrators | Full Control | This folder, subfolders and files |
Inheritance disabled
Auditing
| Type | Principal | Access | Applies |
|---|---|---|---|
| Fail | Everyone | Traverse Folder/Execute File, List folder / Read data, Read attributes, Read extended attributes | This folder, subfolders and files |
| All | Everyone | Create files / Write data, Create folders / Append data, Write attributes, Write extended attributes, Delete subfolders and files, Delete, Change permissions, Take ownership | This folder, subfolders and files |
Inheritance enabled
%SystemRoot%\System32\config\RegBack
Description of policies
Configure this file or folder then: Propagate inheritable permissions to all subfolders and files
Permissions
| Type | Principal | Access | Applies To |
|---|---|---|---|
| Allow | ALL APPLICATION PACKAGES | Read and Execute | This folder, subfolders and files |
| Allow | CREATOR OWNER | Full Control | Subfolders and files only |
| Allow | NT AUTHORITY\SYSTEM | Full Control | Subfolders and files only |
| Allow | BUILTIN\Administrators | Full Control | Subfolders and files only |
Inheritance disabled
Auditing
| Type | Principal | Access | Applies To |
|---|---|---|---|
| Fail | Everyone | Traverse Folder/Execute File, List folder / Read data, Read attributes, Read extended attributes | This folder, subfolders and files |
| All | Everyone | Create files / Write data, Create folders / Append data, Write attributes, Write extended attributes, Delete subfolders and files, Delete, Change permissions, Take ownership | This folder, subfolders and files |
Inheritance enabled
Registry
Computer Configuration → Policies → Windows Settings → Security Settings → Registry
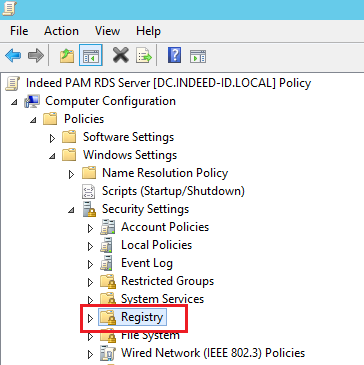
MACHINE\SOFTWARE
Description of policies
Configure this key then: Propagate inheritable permissions to all subkeys
Permissions
| Type | Principal | Access | Applies To |
|---|---|---|---|
| Allow | BUILTIN\Administrators | Full Control | This key and subkeys |
| Allow | CREATOR OWNER | Full Control | Subkeys only |
| Allow | NT AUTHORITY\SYSTEM | Full Control | This key and subkeys |
| Allow | BUILTIN\Users | Read | This key and subkeys |
| Allow | ALL APPLICATION PACKAGES | Read | This key and subkeys |
Inheritance disabled
Auditing
| Type | Principal | Access | Applies To |
|---|---|---|---|
| All | Everyone | Create Subkey, Create Link, Delete, Read permissions, Change permissions | This key and subkeys |
| Success | Everyone | Set Value | This key and subkeys |
Inheritance enabled
MACHINE\SYSTEM
Description of policies
Configure this key then: Propagate inheritable permissions to all subkeys
Permissions
| Type | Principal | Access | Applies To |
|---|---|---|---|
| Allow | BUILTIN\Administrators | Full Control | This key and subkeys |
| Allow | CREATOR OWNER | Full Control | Subkeys only |
| Allow | NT AUTHORITY\SYSTEM | Full Control | This key and subkeys |
| Allow | BUILTIN\Users | Read | This key and subkeys |
| Allow | ALL APPLICATION PACKAGES | Read | This key and subkeys |
Inheritance disabled
Auditing
| Type | Principal | Access | Applies To |
|---|---|---|---|
| All | Everyone | Create Subkey, Create Link, Delete, Read permissions, Change permissions | This key and subkeys |
| Success | Everyone | Set Value | This key and subkeys |
Inheritance enabled
MACHINE\SYSTEM\CurrentControlSet\Control\SecurePipeServers\winreg
Description of policies
Configure this key then: Propagate inheritable permissions to all subkeys
Permissions
| Type | Principal | Access | Applies To |
|---|---|---|---|
| Allow | BUILTIN\Administrators | Full Control | This key and subkeys |
| Allow | CREATOR OWNER | Full Control | Subkeys only |
| Allow | NT AUTHORITY\SYSTEM | Full Control | This key and subkeys |
| Allow | BUILTIN\Users | Read | This key and subkeys |
| Allow | ALL APPLICATION PACKAGES | Read | This key and subkeys |
Inheritance disabled
Auditing
No auditing specified
Advanced Audit Configuration
Computer Configuration → Policies → Windows Settings → Security Settings → Advanced Audit Configuration
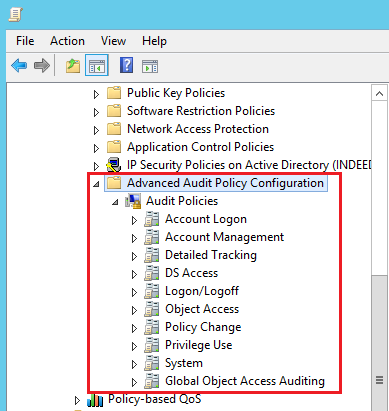
Account Logon
Description of policies
| Policy | Description | Values |
|---|---|---|
| Audit Credential Validation | This policy setting allows you to audit events that occur when validating the login credentials of a user account. Events in this subcategory only occur on computers that are trusted by those credentials. For domain credentials, the domain controller has the appropriate authority. For local accounts, the local computer has the appropriate permissions. | Success, Failure |
| Audit Other Account Logon Events | Other account login events. This policy setting allows you to audit events that occur when responses to user account logon requests that are not related to credential verification and that are not Kerberos tickets are received. | Success, Failure |
Account Management
Description of policies
| Policy | Description | Values |
|---|---|---|
| Audit Application Group Management | This policy setting allows you to audit events that occur when you make the following changes to application groups: Create, edit, or delete an application group. Add or remove a member to an application group. | Success, Failure |
| Audit Computer Account Management | This policy setting allows you to audit events that occur when computer accounts are modified, such as when they are created, modified, or deleted. | Success, Failure |
| Audit Distribution Group Management | This policy setting allows you to audit events that occur when you make the following changes to distribution groups: Create, edit, or delete a distribution group. Add a member to or remove a member from a distribution group. Change the distribution group type. Note. Events in this subcategory are logged only on domain controllers. | Success, Failure |
| Audit Other Account Management Events | This policy setting allows you to audit events that occur when other user account changes are made that are not listed in this category: Accessing the password hash for a user account. This operation is typically performed when migrating passwords using the Active Directory management tool. Call the Password Policy Check API. This function can be called in attacks where a malicious application checks a policy to reduce the number of attempts during a dictionary attack. Changes the default domain group policy to the following group policy paths: Computer Configuration\Windows Settings\Security Options\Account Policies\Password Policies Computer Configuration\Windows Settings\Security Options\Account Settings\Account Lockout Policy Note. A security audit event is logged when the policy setting is applied. No events are logged while parameters are changed. | Success, Failure |
| Audit Security Group Management | This policy setting allows you to audit events that occur when the following security group changes are made: Create, edit, or delete a security group. Add a member to or remove a member from a security group. Changing the group type. | Success, Failure |
| Audit User Account Management | This policy setting allows you to audit changes made to user accounts. The following events are monitored: Create, edit, delete, rename, disable, enable, block and unblock accounts. Set or change the user account password. Adds a security identifier (SID) to the user account SID log. Set a password for Directory Services Restore mode. Change permissions for administrator accounts. Archive or restore Credential Manager credentials. | Success, Failure |
Logon/Logoff
Description of policies
| Policy | Description | Values |
|---|---|---|
| Audit Account Lockout | This policy setting allows you to audit events generated when a logon attempt to a locked account fails. When this policy setting is configured, an audit event is generated when an account cannot log on to a computer because the account is locked. Successful and unsuccessful audit events are recorded in corresponding records. Login events are important for understanding user activity and detecting possible attacks. | Success, Failure |
| Audit Logoff | This policy setting allows you to audit events that occur when a logon session is closed. These events occur on the computer that was accessed. When you log off interactively, a security audit event occurs on the computer that you are logged on to using the user account. When this policy setting is configured, an audit event occurs when the logon session is closed. Successful and unsuccessful attempts to close sessions are recorded in corresponding records. If this policy setting is not configured, no audit events are raised when the logon session is closed. | Success, Failure |
| Audit Logon | This policy setting allows you to audit events that occur when you attempt to log on using a user account. Events in this subcategory are related to the creation of logon sessions and occur on the computer being accessed. When you log on interactively, a security audit event occurs on the computer that you are logged on to using the account. When you log on to a network, for example when accessing a shared folder on the network, a security audit event occurs on the computer that hosts the resource. The following events are monitored: Successful login attempts. Failed login attempts. Attempts to login using explicitly specified credentials. This event occurs when a process attempts to log on to an account by explicitly specifying the appropriate credentials. This event typically occurs in batch logon configurations, such as scheduled tasks or RUNAS commands. Denying logins as a result of security identifier (SID) filtering. | Success, Failure |
| Audit Network Policy Server | This policy setting allows you to audit events that occur when user access requests are made using the RADIUS (IAS) and Network Access Protection (NAP) protocols. Requests for grant, denial, revocation, quarantine, blocking and unblocking are tracked. When this policy setting is configured, an audit event is raised for every IAS or NAP user access request. Successful and unsuccessful user access requests are recorded in corresponding records. | Success, Failure |
| Audit Other Logon/Logoff Events | This policy setting allows you to audit other logon and logout events that are not covered by the Logon/Logout policy setting, for example: Ending Terminal Services sessions. Creating new Terminal Services sessions. Locking and unlocking a workstation. Calling up the screensaver. Disabling the screensaver. Detection of a Kerberos replay attack in which a Kerberos request is sent twice with the same data. This condition may be due to improper network settings. Granting access to a wireless network to a user or computer account. Granting access to a wired 802.1x network to a user or computer account. | Success, Failure |
| Audit Special Logon | This policy setting allows you to audit events that occur when you perform special logon operations such as the following: Using a special login, that is, a login with rights similar to an administrator's, which can be used to elevate a process. Special group member login. When using special groups, audit events are triggered when a member of a specific group logs into the network. You can configure a list of group security identifiers (SIDs) in the registry. An event is logged when one of the specified SIDs is added to the token and that subcategory is enabled. | Success, Failure |
Object Access
Description of policies
| Policy | Description | Values |
|---|---|---|
| Audit Application Generated | This policy setting enables auditing of applications that raise events using the Windows audit APIs. This subcategory is used to log audit events that are associated with the operation of applications that use the Windows audit APIs. The following events in this subcategory are monitored: Creating the application client context. Deleting the application client context. Initializing the application client context. Other application operations using Windows auditing APIs. | Success, Failure |
| Audit Certification Services | This policy setting provides auditing of Active Directory Certificate Services (AD CS) operations. AD CS operations include the following: Starting, shutting down, backing up, and restoring AD CS services. Changing the certificate revocation list (CRL). Requesting for new certificates. Issuing a certificate. Revocation of a certificate. Changing certificate manager settings for AD CS. Changing AD CS services configuration. Changing the Certificate Services template. Importing a certificate. Publishing a CA certificate to Active Directory Domain Services. Changing security permissions for AD CS services. Archiving the key. Importing a key. Removing the key. Starting the OCSP response service. Stopping the OCSP response service. | Success, Failure |
| Audit Detailed File Share | This policy setting allows you to audit attempts to access files and folders in public folders. The option allows you to log events for any attempt to access a file or folder, while the Shared Folders option logs only one event for any connection established between the client and the shared folder. Audit events for this setting include detailed information about permissions or other criteria for granting or denying access. When this setting is configured, an audit event is raised when attempting to access a file or folder in a shared folder. The administrator can enable auditing for success, failure, or both. Note. Public folders do not have system access control lists (SACLs). When this policy setting is enabled, access to all shared files and folders on the system is audited. | Failure |
| Audit File Share | This policy setting allows you to audit attempts to access public folders. When this setting is configured, an audit event is raised when an attempt is made to access a shared folder. When this parameter is set, the administrator can specify that auditing of successes, failures, or both be performed. Note. Public folders do not have system access control lists (SACLs). When this policy setting is enabled, access to all public folders on the system is audited. | Success, Failure |
| Audit File System | This policy setting audits attempts to access file system objects by users. Security audit events occur only for objects that have system access control lists (SACLs) defined, and only if the type of access being requested is write, read, or modify and the requesting account matches the parameters set in the SACL. Note. To set a SACL for a file system object, use the Security tab of the object's Properties dialog box. | Success, Failure |
| Audit Kernel Object | This policy setting provides auditing of attempts to access the kernel using mutexes and semaphores. Security audit events only occur on kernel objects with a corresponding system access control list (SACL). Note. Auditing: The default SACLs for kernel objects are controlled by the Global System Objects access audit setting. | Success, Failure |
| Audit Registry | This policy setting audits attempts to access registry objects. Security audit events occur only for objects that have system access control lists (SACLs) defined, and only if the type of access being requested is read, write, or modify and the requesting account matches the parameters set in the SACL. Note. To set a SACL for a registry object, use the Permissions dialog box. | Success, Failure |
| Audit Removable Storage | This policy setting allows you to audit user attempts to access file system objects on a removable storage device. The security audit event is generated only for all objects and all requested access types. | Success |
| Audit SAM | This policy setting audits events that occur when you attempt to access Security Accounts Manager (SAM) objects. SAM objects include the following: SAM_ALIAS – local group. SAM_GROUP – a group that is not local. SAM_USER – user account. SAM_DOMAIN – domain. SAM_SERVER – computer account. Note. You can only change the system access control list (SACL) for the SAM_SERVER object. | Success, Failure |
Policy Change
Description of policies
| Policy | Description | Values |
|---|---|---|
| Audit Audit Policy Change | This policy setting allows you to audit changes to security audit policy settings, such as the following: Set permissions and audit settings for an audit policy object. Changes in system audit policy. Logging security event sources. Unregistration of security event sources. Changes to audit settings for individual users. Changes in the CrashOnAuditFail parameter value. Changes to the system access control list for a file system or registry object. Changes to the list of special groups. Note. System access control list (SACL) change auditing occurs when the SACL on an object changes and the policy change category is enabled. Auditing of user access control list (DACL) changes and ownership changes occurs when object access auditing is enabled and the object's SACL is configured to audit DACL or ownership changes. | Success, Failure |
| Audit Authentication Policy Change | This policy setting allows you to audit events that occur when you make changes to security groups, such as the following: Create trusts for a forest or domain. Change trust relationships for a forest or domain. Remove trusts for a forest or domain. Changes to the Kerberos policy in the following path: Computer Configuration\Windows Settings\Security Options\Account Policies\Kerberos Policy. Grant a user or group the following priveleges: Access to a computer from the network. Local input. Logging in using Terminal Services. Logging in using a batch job. Login to the service. There is a namespace conflict (for example, if the name of the new trust is the same as the name of an existing namespace). Note. A security audit event is logged when the policy setting is applied. No events are logged while parameters are changed. | Success, Failure |
| Audit Authorization Policy Change | This policy setting allows you to audit events that occur when authorization policy changes are made, such as the following: Assigning privileges to users, such as SeCreateTokenPrivilege, that are not audited in the "Change Authentication Policy" subcategory. Removing user privileges, such as SeCreateTokenPrivilege, that are not audited under the "Change Authentication Policy" subcategory. Encrypting File System (EFS) policy changes. Changes to object resource attributes. Changes to the centralized access policy (CAP) applied to an object. | Success, Failure |
| Audit Filtering Platform Policy Change | This policy setting allows you to audit events that occur when Windows Filtering Platform (WFP) changes are made, such as the following: IPsec service status. Changes to IPsec policy settings. Changes to Windows Firewall policy settings. Changes to suppliers and WFP module. | Success, Failure |
| Audit MPSSVC Rule-Level Policy Change | This policy setting allows you to audit events that occur when policy rules used by the Microsoft Protection Service (MPSSVC) are changed. This service is used by Windows Firewall. The following events are monitored: Messages from active policies when the Windows Firewall service starts. Changes to Windows Firewall rules. Changes to the Windows Firewall exceptions list. Changes to Windows Firewall settings. Rules are skipped or not enforced by the Windows Firewall service. Changes to Windows Firewall Group Policy settings. | Success, Failure |
Privilege Use
Description of policies
| Policy | Description | Values |
|---|---|---|
| Audit Non Sensitive Privilege Use | This policy setting provides auditing of events that occur when privileges that do not affect sensitive data (user priveleges) are used. Using the following privileges does not affect sensitive data: Access the Credential Manager as a trusted caller. Access to a computer from the network. Adding workstations to a domain. Setting memory quotas for a process. Local login. Login through Terminal Services. Bypass cross-validation. Changing the system time. Creating a swap file. Creating global objects. Creating permanent shared objects. Creating symbolic links. Access to the computer from the network is denied. Login as a batch job is denied. Login as a service is denied. Local login is denied. Login through Terminal Services is denied. Force remote shutdown. Increasing the working set of a process. Increasing execution priority. Locking pages in memory. Login in as a batch job. Login as a service. Changing the object's label. Performing volume maintenance tasks. Profiling a single process. System performance profiling. Disconnecting the computer from the docking station. Shutting down the system. Directory service data synchronization. | Success, Failure |
| Audit Sensitive Privilege Use | This policy setting audits events that occur when rights are used that affect sensitive data (user rights) as follows: Call a privileged service. Call one of the following privileges: Action on behalf of an operating system component. Archiving files and directories. Creating a token object. Debugging programs. Enable computer and user accounts that are allowed to delegate. Creating a security audit. Impersonate the client after authentication. Loading and unloading device drivers. Audit and security log management. Changing the value of hardware environment parameters. Process-level token replacement. Recovering files and directories. Changing the owner of a file or other object. | Failure |
System
Description of policies
| Policy | Description | Values |
|---|---|---|
| Audit Other System Events | This policy setting allows you to audit the following events: Starting and stopping the Windows Firewall service and driver. Security policy processing by the Windows Firewall service. Operations with encryption key files and migration operations. | Success, Failure |
| Audit Security State Change | This policy setting allows you to audit events that occur when you make changes to the computer's security state, such as the following: Starting and shutting down the computer. Changing the system time. System recovery for the CrashOnAuditFail event, which is logged after a system restart if the event log is full and the CrashOnAuditFail registry entry is configured. | Success, Failure |
| Audit Security System Extension | This policy setting allows you to audit events related to the security extension, such as the following: Download a security extension, such as an authentication, notification, or security package, and register it with the Local Security Administrator (LSA). It is used to authenticate login attempts, login requests, and any changes to accounts or passwords. Examples of security extensions are Kerberos and NTLM. Install and register the service in Service Control Manager. The audit log records information about the name, binaries, type, startup type, and account of the service. | Success, Failure |
| Audit System Integrity | This policy setting allows you to audit events related to security subsystem integrity violations, such as the following: Events that cannot be recorded in the event log due to errors in the auditing system. Processes that use an invalid local procedure call (LPC) port to impersonate a client by responding to, reading, or writing to the client's address space. Detection of a remote procedure call (RPC) that compromises the integrity of the system. Detection of an invalid executable hash value by a code integrity checker. Encryption operations that violate the integrity of the system. | Success, Failure |
Administrative Templates Section
Computer Configuration → Policies → Administrative Templates
Connections
Windows Components → Remote Desktop Services → Remote Desktop Session Host → Connections
Description of policies
| Policy | Description | Values |
|---|---|---|
| Automatic reconnection | Determines whether Remote Desktop Connection clients are allowed to automatically reconnect to sessions on the Remote Desktop Session Host server when a network connection is temporarily unavailable. By default, you are allowed a maximum of 20 reconnection attempts at 5-second intervals. When set to Enabled, all clients running a Remote Desktop connection attempt to reconnect automatically when a network connection is unavailable. If the setting is set to Disabled, automatic client reconnections are disabled. If the state is set to Not Configured, automatic reconnection is not defined at the Group Policy level. However, users can set up automatic reconnection by selecting the Reconnect when disconnected checkbox on the Interaction tab of the Remote Desktop Connection dialog box. | Disabled |
| Configure keep-alive connection interval | This policy setting allows you to enter a keepalive interval to ensure that the session state on the RD Session Host server matches that of the client. After a RD Session Host server client loses connectivity to an RD Session Host server, the session on that server can remain active rather than going into a disconnected state, even if the client is physically disconnected from the RD Session Host server. If the client logs on to the same RD Session Host server again, a new session may be established (if the RD Session Host server is configured to allow multiple sessions) and the original session may still be active. If this policy setting is enabled, a keepalive interval must be entered. The keepalive interval determines how often (in minutes) the server checks the session state. Valid values range from 1 to 999 999. If this policy setting is disabled or not configured, the keepalive interval is not set and the server does not check session state. | Enabled Keep-Alive interval: 1 |
| Set rules for remote control of Remote Desktop Services user sessions | When you enable this policy setting, administrators can interact with a user's Remote Desktop Services session based on the option they select. Select your desired level of control and permissions from the list of options: Remote control not allowed: Prevents the administrator from using remote control or viewing remote user sessions. Full control with user permission: Allows the administrator to interact with the session, subject to the user's consent. Full control without user permission: Allows the administrator to interact with the session even without the user's consent. Monitor session with user permission: Allows an administrator to view a remote user's session with the user's consent. Monitor session without user permission: Allows an administrator to view a remote user's session without the user's consent. If you disable this policy setting, administrators can interact with a user's Remote Desktop Services session if the user consents. | Enabled Options: Full Control without user's permission |
Device and Resource Redirection
Windows Components → Remote Desktop Services → Remote Desktop Session Host → Device and Resource Redirection
Description of policies
| Policy | Description | Values |
|---|---|---|
| Do not allow COM port redirection | Determines whether data redirection from the remote computer to client COM ports should be disabled in Remote Desktop Services sessions. You can use this policy setting to prevent users from redirecting data to peripheral devices connected to COM ports or mapping local COM ports when connecting to a Remote Desktop Services session. By default, Remote Desktop Services allows data redirection to COM ports. If you enable this policy setting, users cannot forward server data to the COM ports of local computers. If you disable this policy setting, COM port redirection is always allowed by Remote Desktop Services. If you do not configure this policy setting, COM port redirection is not defined at the Group Policy level. | Enabled |
| Do not allow LPT port redirection | This policy setting determines whether data forwarding to client LPT ports in Remote Desktop Services sessions should be disabled. This policy setting can be used to prevent users from mapping local LPT ports and redirecting data from a remote computer to local peripheral devices connected to LPT ports. By default, Remote Desktop Services allows LPT port forwarding. If you enable this policy setting, users during a Remote Desktop Services session cannot forward server data to local LPT ports. If you disable this policy setting, redirection to LPT ports is always allowed. If you do not configure this policy setting, LPT port redirection is not defined at the Group Policy level. | Enabled |
| Do not allow supported Plug and Play device redirection | This policy setting allows you to control whether supported Plug and Play devices, such as Windows Portable Devices, are redirected to a remote computer during a Remote Desktop Services session. By default, Remote Desktop Services allows redirection of supported Plug and Play devices.Users can use the Advanced setting on the Local Resources tab of the Remote Desktop Connection dialog box to select supported plug-and-play devices to redirect to the remote computer. If you enable this policy setting, users cannot redirect supported Plug and Play devices to a remote computer. If you disable or do not configure this policy setting, users can redirect supported Plug and Play devices to the remote computer. Note. You can use policy settings in the Computer Configuration\Administrative Templates\System\Device Installation\Device Installation Restrictions folder to prevent redirection of certain types of supported Plug and Play devices. | Enabled |
Remote Session Environment
Windows Components → Remote Desktop Services → Remote Desktop Session Host → Remote Session Environment
Description of policies
| Policy | Description | Values |
|---|---|---|
| Remove "Disconnect" option from Shut Down dialog | This policy setting allows you to remove the "Disconnect Session" item from the Shut Down Windows dialog box in Remote Desktop Services sessions. By using this policy setting, you can prevent users from using this familiar method of disconnecting a client computer from the Remote Desktop Session Host server. When this policy setting is enabled, the Disconnect Session option does not appear in the drop-down list in the Shut Down Windows dialog box. If this policy setting is disabled or not configured, the Disconnect Session item is not removed from the list in the Shut down Windows dialog box. Note. This policy setting only affects the Shut Down Windows dialog box. It does not prevent users from using other methods to disconnect from a Remote Desktop Services session. This policy setting also does not prevent sessions from being disconnected on the server. You can set the period of time that a disconnected session will remain active on the server by configuring the setting: Computer Configuration\Administrative Templates\Windows Components\Remote Desktop Services\Remote Desktop Session Host\Session Time Limits\Set Time Limit. | Enabled |
| Remove Windows Security item from Start menu | Determines whether the Windows Security item should be removed from the Options menu on Remote Desktop Services clients. You can use this policy setting to prevent insufficiently experienced users from being inadvertently disconnected from Remote Desktop Services. When set to Enabled, Windows Security does not appear in the Start menu. As a result, in order to open the Windows Security dialog box on the client computer, the user must use a special keyboard shortcut (CTRL+ALT+END). If the setting is set to Disabled or Not Configured, Windows Security remains in the Start menu. | Enabled |
Security
Windows Components → Remote Desktop Services → Remote Desktop Session Host → Security
Description of policies
| Policy | Description | Values |
|---|---|---|
| Require secure RPC communication | Indicates whether the Remote Desktop Session Host server requires secure RPC connections from all clients or allows insecure connections. This setting can be used to improve the security of client RPC connections by allowing only authenticated and encrypted requests. When the status is Enabled, Remote Desktop Services accepts requests only from RPC clients that support secure requests and does not allow insecure connections from untrusted clients. When the status is Disabled, Remote Desktop Services always requests that all RPC traffic be sent securely. If the status is Not Configured, insecure connections are allowed. Note. The RPC interface is used to administer and configure Remote Desktop Services. | Enabled |
| Set client connection encryption level | This policy setting determines whether a special level of encryption is required for secure communications between client computers and RD Session Host servers during remote RDP connections. If you enable this policy setting, all communications between clients and RD Session Host servers during remote connections must use the encryption method that is specified in this setting. The default encryption level is set to High. The following encryption methods are supported: High. A value of "High" means that data exchanged between the client and server is encrypted using strong 128-bit encryption. Use this level in environments that contain only 128-bit clients (for example, clients using the Remote Desktop Connection service). Clients that do not support this level of encryption cannot connect to Remote Desktop Session Host servers. Client compatible. A value of "Client Compatible" means that data exchanged between the client and server is encrypted using the strongest key supported by the client. Use this level of encryption in environments with clients that do not support 128-bit encryption. Low. When set to Low, only data sent from the client to the server is encrypted using 56-bit encryption. If the setting is disabled or not configured, Group Policy does not control the level of encryption used for remote connections to Remote Desktop Session Host servers. Important! FIPS compliance can be configured through System Encryption Tools. Use FIPS-compliant algorithms for encryption, hashing, and digital signature settings in Group Policy (Computer Configuration\Windows Settings\Security Options\Local Policies\Security Options). The FIPS Compliant setting encrypts and decrypts data sent from the client to the server and back using FIPS 140-1 (Federal Information Processing Standard) encryption algorithms using Microsoft encryption modules. Use this level of encryption for communications between clients and RD Session Host servers that require the highest level of encryption. | Enabled Encryption Level: High Level |
Session Time Limits
Windows Components → Remote Desktop Services → Remote Desktop Session Host → Session Time Limits
Description of policies
| Policy | Description | Values |
|---|---|---|
| End session when time limits are reached | This policy setting determines whether a Remote Desktop Services session is timed out instead of disconnected. You can use this setting to force a Remote Desktop Services session to end (which forces the user to log off and the session information is deleted from the server) when the active or inactive session limit is reached. By default, Remote Desktop Services disconnects sessions after their specified session time has expired. Time limits are enforced by the server administrator locally or through Group Policy. See the policy settings "Set a time limit for active Remote Desktop Services sessions" and "Set a time limit for active but idle Remote Desktop Services sessions." If you enable this policy setting, Remote Desktop Services terminates all timed-out sessions. If you disable this policy setting, Remote Desktop Services always disconnects sessions that time out, even if your server administrator has specified different behavior for this policy setting. If you do not configure this policy setting, Remote Desktop Services disconnects sessions that time out, unless otherwise specified in local settings. Note. This policy setting applies only to administrator-defined timeout restrictions. This policy setting does not apply to timeout events that are determined by network connection conditions. This option is available in the Computer Configuration and User Configuration folders. If both settings are configured, the setting in the Computer Configuration folder takes priority. | Enabled |
| Set time limit for disconnected sessions | This policy setting allows you to configure a time limit for disconnected Remote Desktop Services sessions. This policy setting allows you to define the maximum period of time that a disconnected session remains active on the server. By default, Remote Desktop Services allows users to disconnect from a Remote Desktop Services session without ending or logging out of the session. When a session is in a disconnected state, running programs continue to run even though the user is not connected. By default, such disconnected sessions remain open on the server indefinitely. If you enable this policy setting, disconnected sessions are deleted from the server after the specified time. To ensure the default behavior that disconnected sessions are serviced without time limit, select Never. For a console session, time limits do not apply to disconnected sessions. If you disable or do not configure this policy setting, it is not defined at the Group Policy level. By default, disconnected Remote Desktop Services sessions remain opened without time limits. Note. This setting is located in the Computer Configuration and User Configuration folders. If policy settings are specified in both folders, the setting in the Computer Configuration folder takes precedence. | Enabled End a disconnected session: 1 minute |
Temporary Folders
Windows Components → Remote Desktop Services → Remote Desktop Session Host → Temporary folders
Description of policies
| Policy | Description | Values |
|---|---|---|
| Do not delete temp folders upon exit | This policy setting determines whether Remote Desktop Services temporary folders are saved after sessions end. This policy setting allows temporary user session folders to remain on the remote computer even after the session ends. By default, Remote Desktop Services deletes users' temporary folders when the user logs off. If you enable this policy setting, temporary user session folders are not deleted when sessions end. If you disable this policy setting, temporary folders are deleted when the session ends, even if the server administrator has specified otherwise. If you do not configure this policy setting, Remote Desktop Services deletes temporary folders from the remote computer when you log off, unless otherwise specified by the server administrator. Note. This setting is only relevant if the server uses temporary session folders. If the "Do not use temporary folders for session" policy setting is enabled, this setting has no effect. | Disabled |
| Do not use temporary folders per session | This policy setting prevents Remote Desktop Services from creating temporary session folders. This policy setting allows you to prevent the remote computer from creating separate temporary folders for each session. By default, Remote Desktop Services creates a separate temporary folder for each active user session on the remote computer. Such temporary folders are created on the remote computer in the Temp folder of the user profile folder and are named after the session code. If you enable this policy setting, temporary session folders are not created. Instead, the user's temporary files for all sessions on the remote computer are stored in the Temp shared folder of the user's profile folder on the remote computer. If you disable this policy setting, separate temporary folders are always created for each session, even if a different mode is specified by the server administrator. If you do not configure this policy setting, separate temporary folders are created for each session unless a different mode is specified by the server administrator. | Disabled |
Policies Import Procedure
- On the domain controller, create a new GPO, for example "Axidian Privilege RDS Server".
- Configure GPO security filters to apply only to the Axidian Privilege Gateway server object.
- Download the archive with a set of policies and unpack it into a temporary folder.
- Right-click on the created GPO and select "Import settings..." from the context menu.
- Specify the path to the folder with the unpacked archive.
- In the "Transfer Links" window, select the "copy them exactly from source" checkbox.
- After successful import, open the GPO and edit the "Allow log on through Remote Desktop Services" policy by adding a security group for users who need remote access.
- Link the GPO to the organizational unit that owns the Axidian Privilege Gateway server.
- Apply the policies by running the gpupdate /force command on the Axidian Privilege Gateway server.